Creating an IP entity enrichment layer
using GreyNoise Community API and Automation Rules feature on Azure Sentinel
While investigating Azure Sentinel’s new Automation rules to work with Azure Sentinel Incidents, I wanted to see if you could build a entity enrichment layer. This concept could be used for any Azure Sentinel incident being created and enriching the entities with additional information back into Custom log tables, HTML Comments, and also raising or lowering the severity based on factors.
To use this Playbook checkout here
To start I found that GreyNoise recently released a Community API. With this API you can pass in IP entities and enrich them with further information.
A little about GreyNoise . GreyNoise deploys thousands of sensors across the internet among different providers and platforms to collect and harvest a vast threat intelligence feed around various Internet signals and noises. The goal is that SOCs using SIEMs like Azure Sentinel can take advantage of this knowledge and look up the IP address to rule it out (RIOT) and if it is not a common public IP address, then provide IP Context information via an API call. This allows for IP entities discovered in an incident to be checked if the IP was seen before and detailed information around the IP address and what GreyNoise’s proprietary sensors discovered during contact. What is also of interest is when an IP address has not been identified by GreyNoise. This could potentially indicate a specialized attack that is ongoing in your environment as it is not normal bot activity discovered by GreyNoise.
Using GreyNoise’s logic scenario as a template this new Playbook will provide an enrichment layer for incoming Azure Sentinel Incidents with IPs.
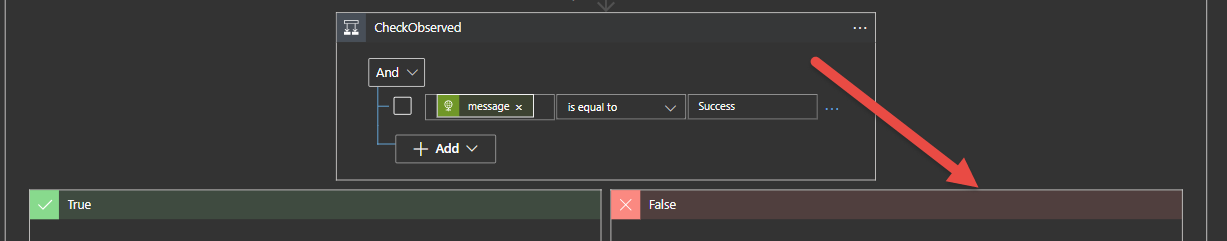
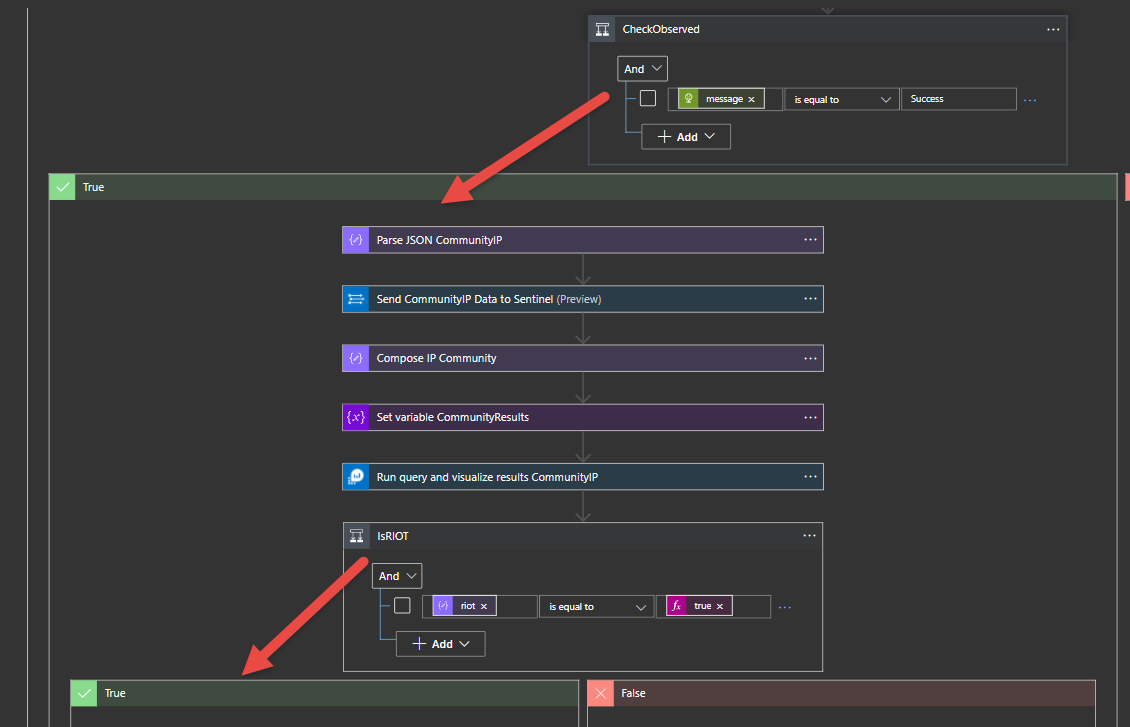
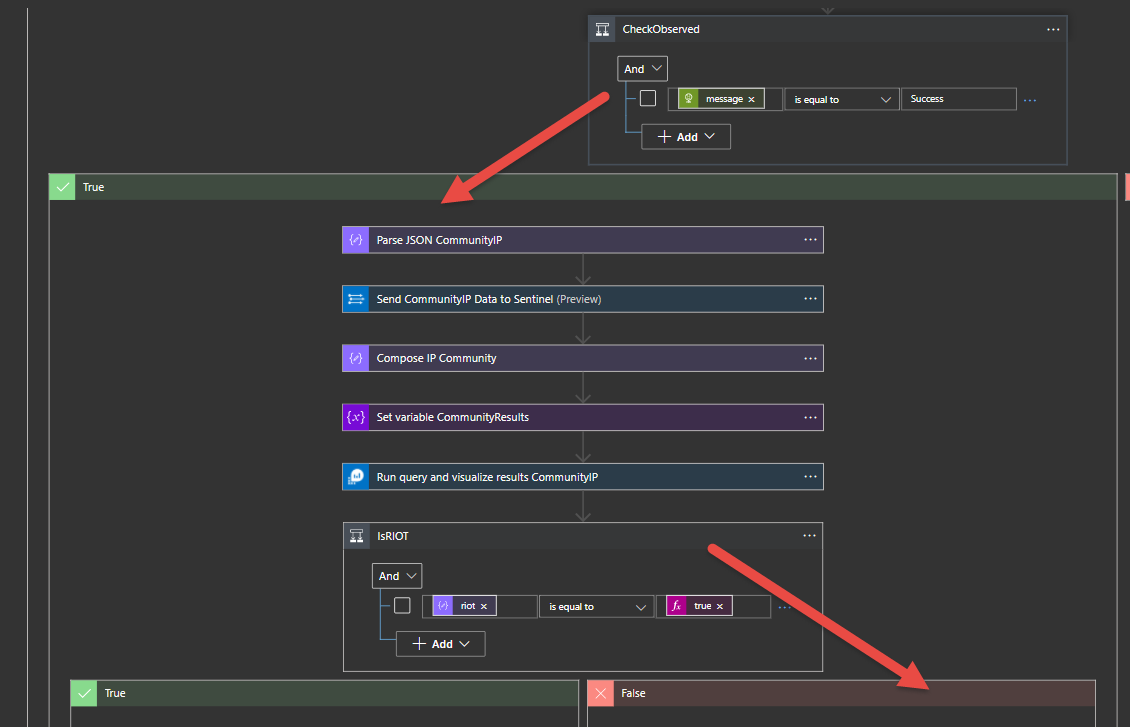
The following logic occurs.
For each IP Entity check the IP against the GreyNoise Community API
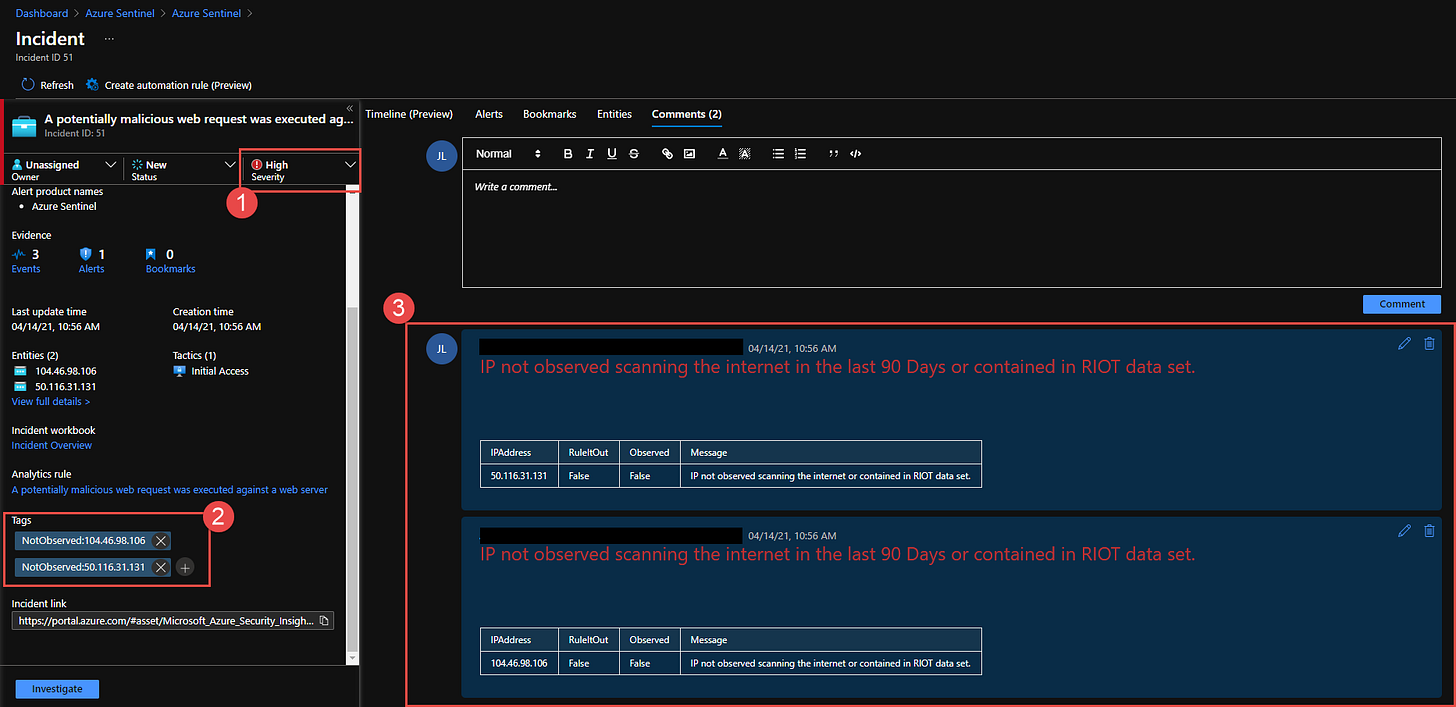
If the IP is not found in the Rule it Out (RIOT) database or observed from the sensors then update the Azure Sentinel Incident with HTML Comments, a Tag that the IP is NotObserved and raise the severity as High as this could be a unique threat.
If the IP is discovered the playbook will check to see if it was found in the Rule it Out (RIOT) Database.
If found in the Rule it Out (RIOT) Database then Tag the incident with IP ObservedRIOT, lower the severity of incident since this is most likely a benign IP Address, add HTML Comments, and a GreyNoise visualizer link
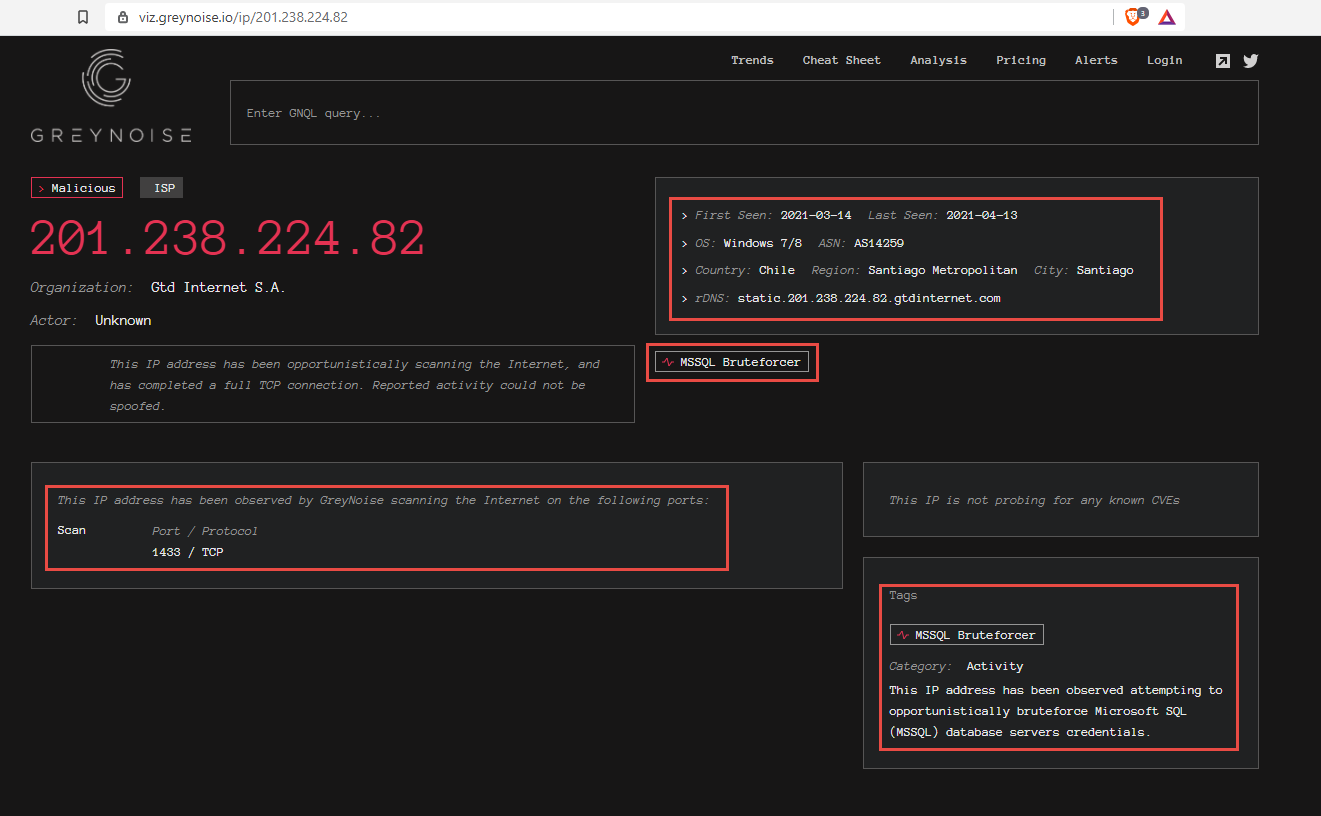
If the IP is not found in Rule it Out (RIOT) then GreyNoise has seen this IP in the sensors within the last 90 days, it could be a scanner, bot, or other activity. A classification does get labeled to the IP.
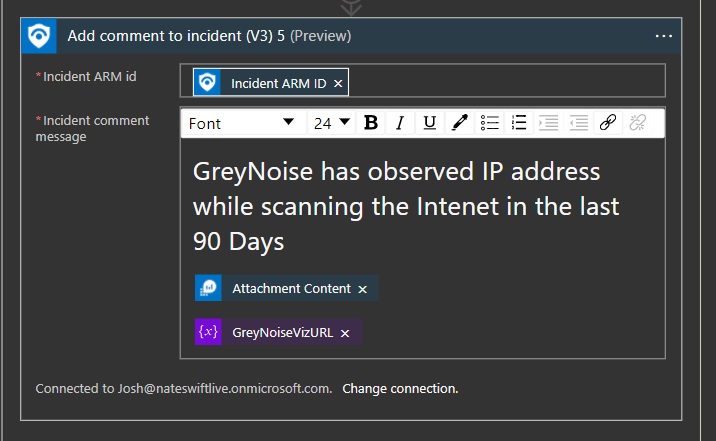
Add a HTML Comment to the Sentinel incident with a visualizer link
The visualizer link will have more details on what the GreyNoise scanners have seen from the Internet and this IP.
Other enrichment layers could be built for other entities as well for URLs, Accounts, FileHashes\Files, others.
In addition to the Community API Playbook another GreyNoise Playbook was created if you happen to have a GreyNoise API Key. This Playbook stamps more data into the HTML Comments and Custom Logs as it invokes the GreyNoise RIOT API and IP Context API and gets more data back.