Remix with a Twist: 7 steps to author, develop, and deploy custom recommendations for Windows using Guest Configuration
How I Learned to Stop Worrying and Love Azure Policy
The following article is a remix and a twist from: 7 steps to author, develop, and deploy custom recommendations for Windows using Guest Configuration
While working with some customers they enjoy the many benefits of Microsoft Defender for Endpoint using features like Advanced Threat Hunting logs or Threat Vulnerability Management reporting…
However they may have a 3rd party AV product they are leveraging in cloud based servers like EC2 or Azure VMs and on-premise servers. Defender for Cloud offers Defender for Servers and with a little Azure Policy it can remediate and push MDE with the newer Unified agent, installing Defender for AV on Windows Servers 2012R2 and Server 2016.
When pushed the Defender for AV is deployed in a active mode for Windows Server, and in cases with 3rd party AV this can at times cause race conditions and performance issues to the Windows Server. It’s best to put Defender for AV in Passive mode if a 3rd Party AV is present and being used by the enterprise.
In cases where customers want to leverage their 3rd Party AV but still use MDE you can use Azure Policy and Guest Configuration to programmatically check and set Passive Mode for Defender for AV on those Windows Servers in Azure and Servers connected via Azure Arc receiving Defender for Endpoint through auto provision in Defender for Cloud.
Prerequisite:
In order to take advantage of this capability you must ensure that Guest Configuration extension is deployed to your Azure VMs and Azure Arc Connected servers. For enterprises you will want to take advantage of native built in capabilities like Auto provisioning the Guest Configuration extension in Microsoft Defender for Cloud. This way as new VMs are created or deallocated VMs are turned on they will also receive the Guest Configuration.
With the Guest Configuration extension set to deploy a variety of opportunities to check for your organizations software requirements and settings inside the OS awaits.
Development Process:
Overall, there is 7 steps documented process to author, develop, and deploy; this blog will summarize each step however will link to each Azure Doc along that step so you can get full details if desired.
Steps 1 through 6 are done in an Authoring VM with PowerShell.
Step 7 is done in the Microsoft Defender for Cloud portal, but could be done through PowerShell, this would allow a DevOps approach to existing and new subscriptions coming online.
4 of these steps are used to produce the Desired State Configuration files for Guest Configuration.
Steps 5 and 6 use PowerShell to create the custom Guest Configuration Azure Policy and publish it to your subscription.
Step 1: build Authoring VM and Author DSC checking for a windows service
To start be sure to use the following Azure documentation to create a Azure VM that will host the Authoring tools and software to work with Guest Configuration. The key here is a Azure VM with Windows 10 or Windows Server. You will want to install the following:
Download and Install PowerShell 7.1.3 or higher:
https://github.com/PowerShell/PowerShell/releases/download/v7.1.3/PowerShell-7.1.3-win-x64.msi
Be sure to install any software you want to detect in our example you can install through cmdline Nessus Agent
Using the PowerShell 7 (x64) console, install the following modules:
Install-Module AzInstall-Module GuestConfigurationInstall-Module PSDscResourcesImport-Module GuestConfigurationImport-Module PSDscResourcesOnce you have the tools installed and ready to go you can open up any text editor VS Code, Notepad, or PowerShell ISE console. The following below is used for checking a Windows Service, since most AV or Vulnerability scanning software on servers leverage a Windows Service and are always running this may be the easiest way to detect.
configuration WDAVPassive
{
Import-DscResource -ModuleName PSDscResources
Node localhost
{
Service ApexOneNTRealTimeScan #Rename for 3rdParty AV
{
Name = "ntrtscan" #Rename for 3rdParty AV service
StartupType = "Automatic"
State = "Running"
Ensure = "Present"
}
Registry WDAVPassiveValueSet
{
DependsOn = '[Service]ApexOneNTRealTimeScan' #Rename for DSC Service name line 7, used to check for 3rd party av before applying reg change
Key = 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection'
Ensure = 'Present'
ValueName = 'ForceDefenderPassiveMode'
ValueType = 'DWord'
ValueData = '1'
Force = $true
}
}
}
Save the file as WDAVPassive.ps1 . You have just created a DSC based powerShell script. DSC with Guest Configuration has many other states to check for, please use the PSDSCResources module as it works with Guest Configuration. Use the following website to see other states to check for: PowerShell/PSDscResources (github.com)
Step 2: Compile DSC .ps1 to generate the .mof state file
Using the PowerShell 7 (x64) console use the following PS commands to load the DSC into memory and compile the .mof file
. .\WindowsNessusAgentService.ps1
WindowsNessusAgentService
Afterwards a folder should be created called WindowsNessusAgentService and within the folder a compiled localhost.mof file. Open the localhost.mof file in a text editor and take a look, you may want to remove or update author as this is the account name on the VM used to generate the .mof file.
Step 3: Create a Guest Configuration package .zip file
In this next step you will use the cmdlets from the GuestConfiguration module to generate a package using the .mof and zip the data into a archive for Azure Policy Guest Configuration.
New-GuestConfigurationPackage `
-Name 'WindowsNessusAgentService' `
-Configuration './WDAVPassive/localhost.mof' `
-Type AuditandSet `
-Force
Step 4: Test Guest Configuration policy in local environment
You want to be sure that the Guest Configuration will execute DSC properly and if the DSC results occur as desired. To do this use the following GuestConfiguration PS cmdlet to test the package.
Start-GuestConfigurationPackageRemediation -Path ./WDAVPassive/WDAVPassive.zip
Step 5: Publish custom Guest Configuration package to Azure Blob Storage
In this step you will log into Azure, Create a Storage Account, and Container, and craft a SAS Signaturecmdlet to upload the .zip package you tested previously to a Azure Blob Storage account – in addition a blob uri will be returned with a sas signature that lasts a few years. This sas based signature will be used when creating the Azure policy and publishing it in the next step.
# Creates a new resource group, storage account, and container
New-AzResourceGroup -name rgGuestConfiguration -Location WestUS
New-AzStorageAccount -ResourceGroupName rgGuestConfiguration -Name xxxguestconfigstorage-SkuName 'Standard_LRS' -Location 'WestUs' | New-AzStorageContainer -Name guestconfiguration -Permission Blob
$Context = New-AzStorageContext -ConnectionString "DefaultEndpointsProtocol=https;AccountName=ContosoGeneral;AccountKey=< Storage Key for ContosoGeneral ends with == >;"
Set-AzStorageBlobContent -Container "guestconfiguration" -File ./WDAVPassive.zip -Context $Context
$StartTime = Get-Date
$EndTime = $startTime.AddYears(3)
$contenturi = New-AzStorageBlobSASToken -StartTime $StartTime -ExpiryTime $EndTime -Container "guestconfiguration" -Blob "WDAVPassive.zip" -Permission rwd -Context $Context –FullUri
Copy the SAS URL Signature from $contenturi
Step 6: Create the custom Azure Policy definition id
In this next step we are going to take the Guest Configuration package in Azure Blob Storage and use it to define a new custom Azure Policy definition. Start with creating a new guid.
$Guid= New-Guid
With the new guid and sas blob uri use the following ps cmdlets and replace where necessary.
$BlobSASUUri = “REPLACE from Above $contenturi use the URL SAS Signature”
New-GuestConfigurationPolicy `
-PolicyId $Guid `
-ContentUri $BlobSASUUri `
-DisplayName 'Windows Check 3rd Party AV - Set WDAV Passive' `
-Description 'Setup WDAV Passive Mode if certain 3rd party AV is installed' `
-Path './policies' `
-Mode ApplyAndAutoCorrect `
-Platform 'Windows' `
-PolicyVersion 1.0.0 `
-Verbose
Now the that the custom Policy definition has been created with a policies folder and .json run this last command to create the Guest Configuration policy in Azure Subscription
New-AzPolicyDefinition -Name 'WDAVPassive' -Policy '.\policies\WDAVPassive_DeployIfNotExists.json'
Step 7: Use Azure Policy Assignment
Now that the custom policy definition using Guest Configuration is set in Azure, Click Step 7 link above to Assign the Policy for the Azure Windows Servers and Azure Arc connected Windows servers
Alternative: Using Defender for Cloud create a custom security recommendation
Now that you deployed and created a new custom Azure Policy using Guest Configuration, you can deploy the policy to check Windows VMs on Azure and Azure Arc enabled for the 3rd Party AV software and if found deploy the registry change to put WDAV in passive mode. In effect you have a Azure plane using Azure Policy to check for compliance and in more advanced cases using DSC check and change or install software inside the operating system – recall the PSDscResource module and it’s capabilities. PowerShell/PSDscResources (github.com). You have a outer Azure Policy set and managed a cloud scale your inner servers settings.
The last step is that non compliant states can be sent to Defender for Cloud in the form of Custom security recommendations .
In this last step go to Microsoft Defender for Cloud in the Azure portal and click on the left hand blade environment settings.
Search for your Azure Subscription you deployed the custom Guest Configuration Azure Policy and click on the subscription
Click on the Security policy on the left blade and scroll down and click on Add a custom initiative
Fill in information, choose the existing category Security Center
Choose Add policy definitions, filter on custom and choose your uploaded custom Azure Policy at the bottom of the right hand blade click add.
Click next until the Policy parameters, uncheck only show parameters that need input or review. You can now extend support to Azure Arc connected servers. By setting these values.
Afterwards you add the new custom initiative and Create new.
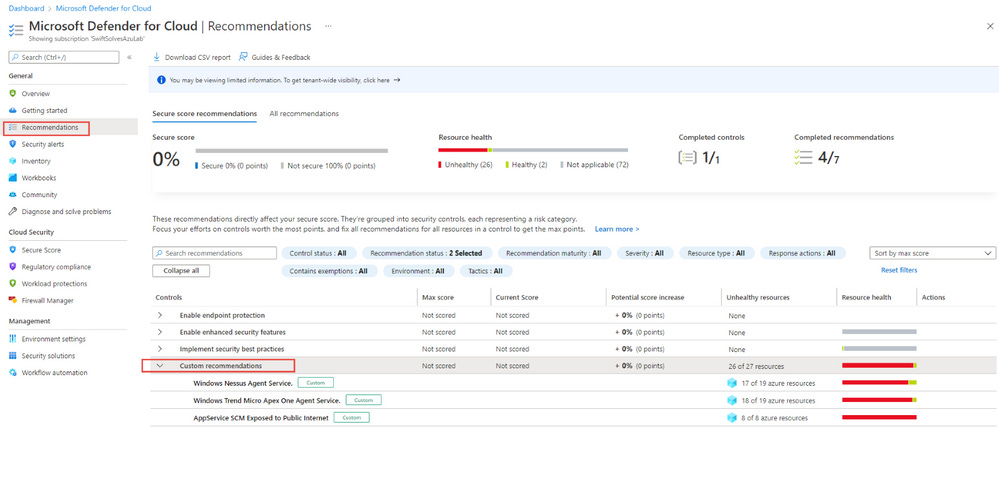
Now that you have connected and assigned the custom Guest Configuration Azure Policy to your subscription through Microsoft Defender for Cloud, within the recommendations screen you will now have timely (refresh every 30 minutes) accurate checks for Nessus software installed.
Some additional things to consider:
In Step 3 when generating the package .zip you can set –Type from Audit to AuditandSet which will also update the settings in the VM to match the desired state.
In PSDResources module there is a method for MSI Installer
Use Workflow Automation in some unique ways or a Logic App to generate a report to be emailed in html.
Take a DevOps approach as new Subscriptions come online generate the Guest Configuration policy definition in subscription and assign through Defender for Cloud custom initiatives.
Full 7 steps in authoring VM showing PS cmdlets involved.
Start thinking of the ways you can use PSDResources to craft your own Security recommendations and configurations across your hybrid clouds and on-premise servers.